AES-128 consists of a total of 10 rounds, in which the operations SubBytes, ShiftRows, MixColumns, and AddRoundKey are repeated. Before these rounds can be executed, the original 128-bit key is expanded into eleven separate round keys through the AES key schedule. Each round then uses one of these derived keys in the AddRoundKey step, ensuring that the secret key material influences every stage of the encryption.
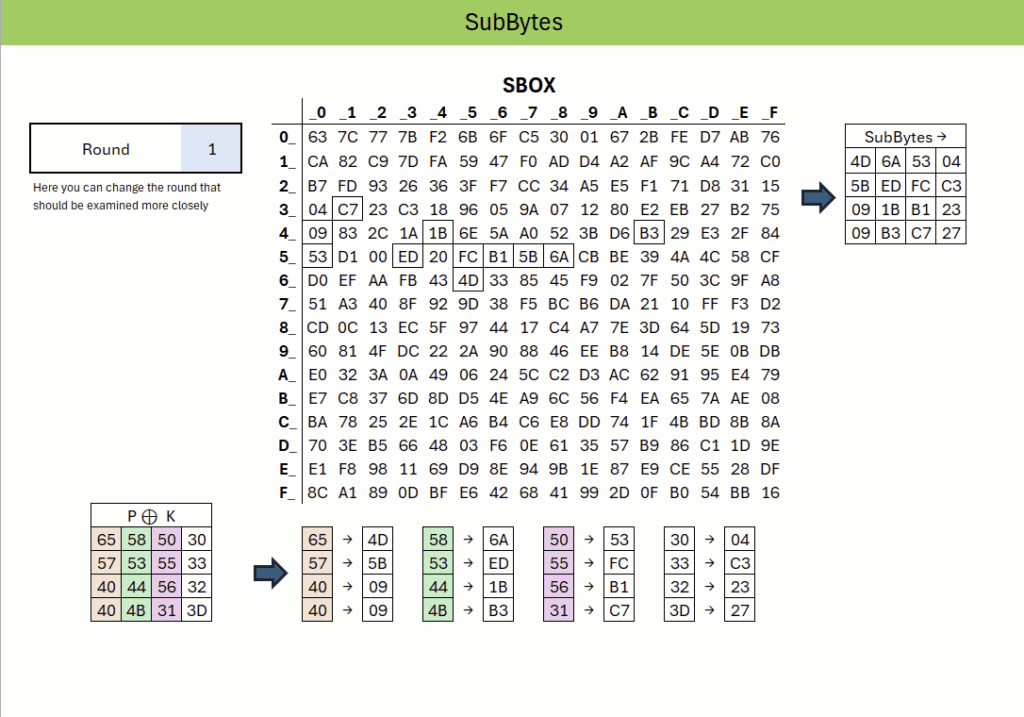
First, during the SubBytes step, every byte is substituted with a new value from a nonlinear substitution table, the so-called S-box. This introduces non-linearity into the algorithm and makes the cipher resistant to simple algebraic attacks.
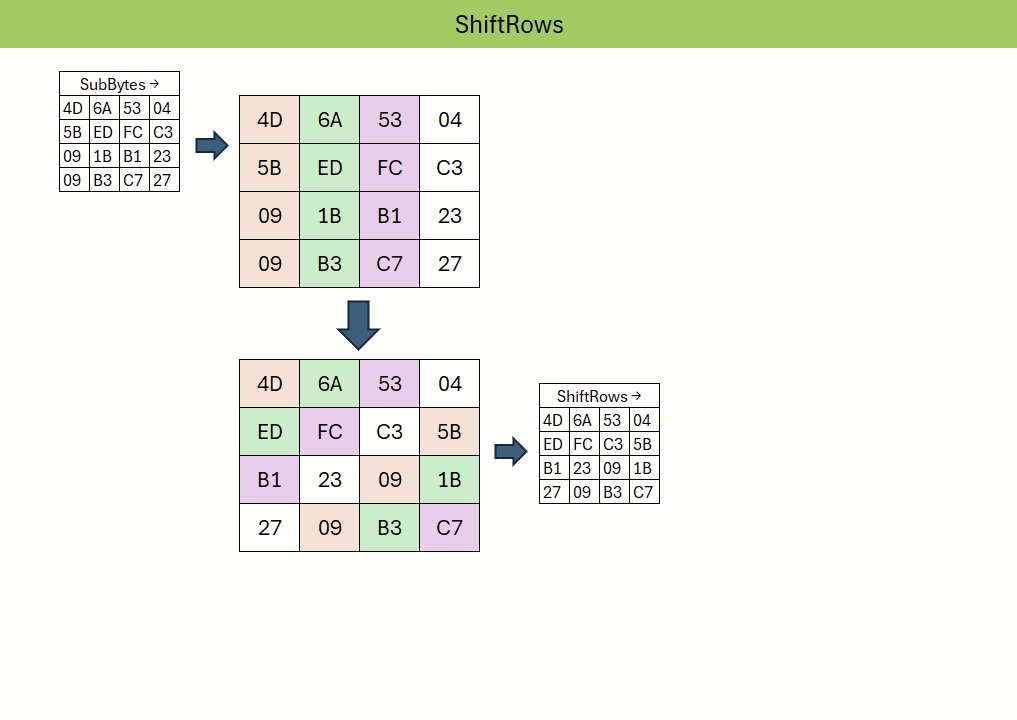
Next, the ShiftRows operation cyclically shifts the rows of the state matrix by different offsets. This ensures that bytes are moved across columns, thereby contributing to diffusion and spreading local changes throughout the block.
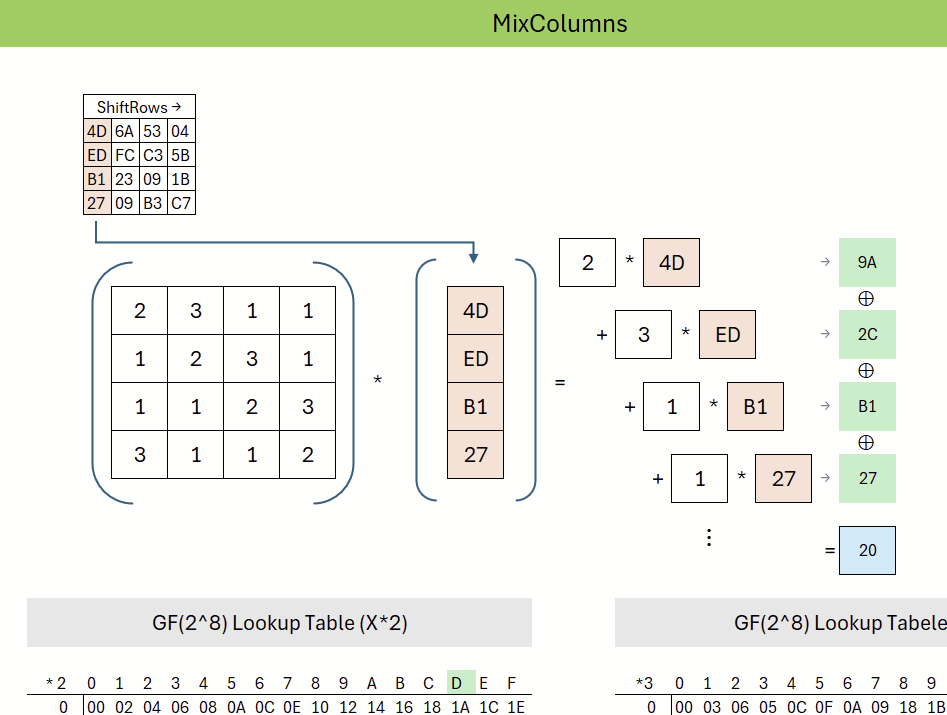
The following step, MixColumns, treats each column of the state as a polynomial and transforms it through a fixed matrix multiplication in the finite field GF(2^8). This step further mixes the data and ensures that bits are spread more evenly across the state.
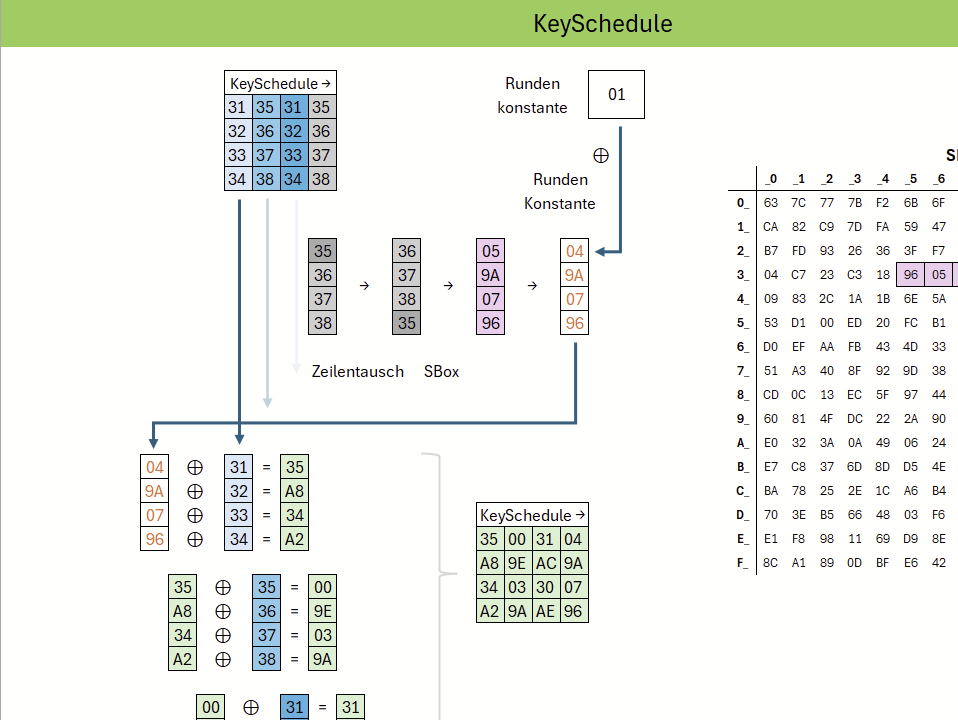
The AES KeySchedule generates the round keys from the original cipher key. This is done by repeatedly transforming parts of the key: bytes are rotated, substituted using the S-box, and combined with round constants before being XORed with earlier key material. As a result, each round uses a unique key, while still being linked to the original secret key.
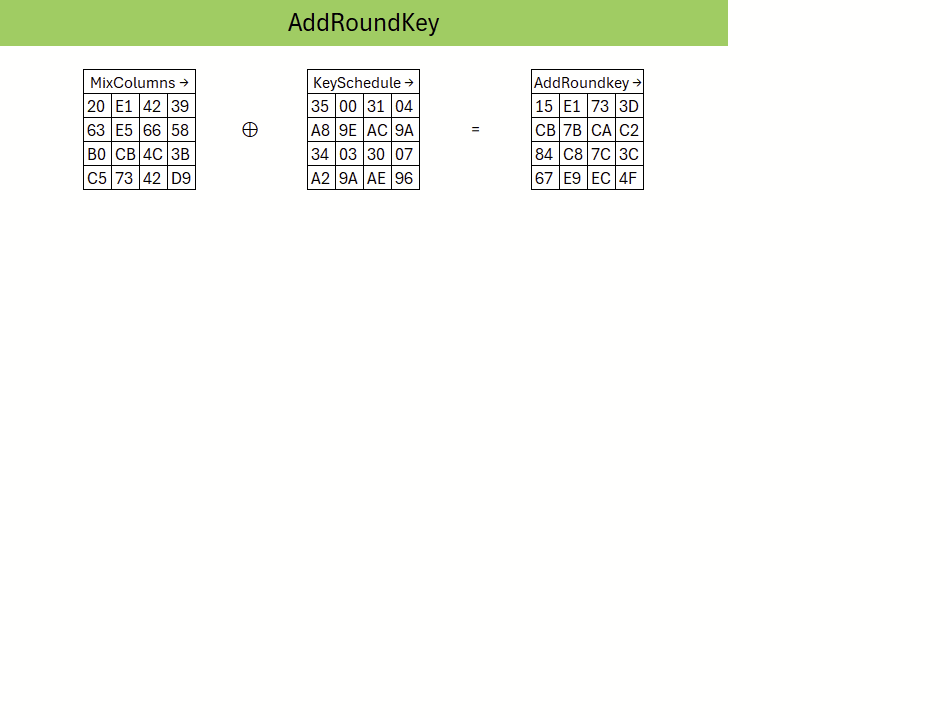
Finally, in the AddRoundKey stage, the state is combined with the round key by applying an XOR operation. This is the point at which the secret key material enters the round transformation and secures the data against unauthorized decryption.
To provide better insight into these operations, a complete implementation of AES is made available here. In addition, the first round is presented in detail across the individual tabs.
Download of the Microsoft Excel file. Macros were avoided; however, due to the use of Lambda functions, the result will only run under Office 365 or Excel 2024.
SHA256: 1BB1037BC35D86D3E7BBE31C80C2801912F3E84598E7FB2AFE0DB116DF0CFE56
